Secret Language of Code
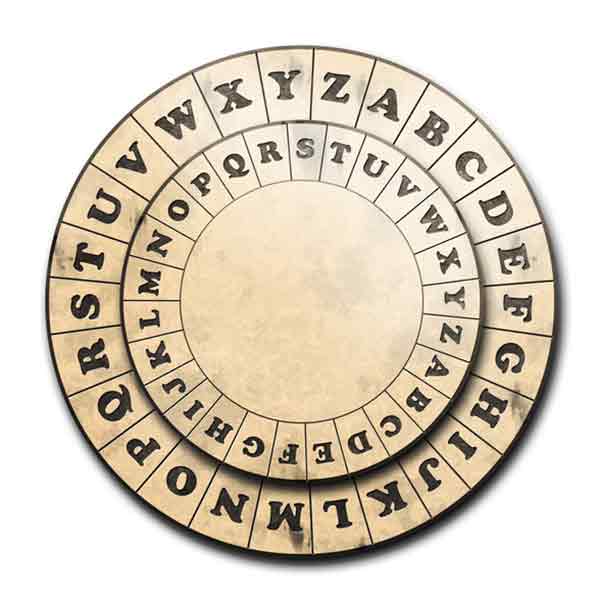
Caesar Cipher Wheel (kprojekt, Getty Images)

Caesar Cipher Wheel (kprojekt, Getty Images)
How does this align with my curriculum?
| Grade | Course | Topic |
|---|
Students will learn how cryptography and encryption are used to protect personal data and use cryptography to code and decode messages.
Overview
| Activities | Timing | Student grouping | Description |
|---|---|---|---|
| Minds-On: Understanding Data Encryption | 10 minutes | Individual | Students will reflect on what they know about data encryption. |
| Action: Cipher Activity | 30 minutes | Small Group | Students will create and decode a simple cipher. |
| Consolidation: Knowledge Debrief | 10 minutes | Large group or Independent | Students will discuss concepts explored during the activities. |
This lesson can be done over a few days.
Students will:
- Understand what is meant by encryption
- Understand how encryption can be used to keep data safe
- Understand different ways that data can be encrypted
Learning Goals
Students will:
- Understand what is meant by encryption
- Understand how encryption can be used to keep data safe
- Understand different ways that data can be encrypted
Students can:
- Explain why it is important to encrypt data
- Relate the practice of encryption to their own lives
- Use analytical and problem-solving skills to encrypt and decrypt simple messages
Success Criteria
Students can:
- Explain why it is important to encrypt data
- Relate the practice of encryption to their own lives
- Use analytical and problem-solving skills to encrypt and decrypt simple messages
This icon indicates potential assessment opportunities.
Observations
- Observe how students use analytical and problem-solving skills as they encrypt and decrypt simple messages
- Observe the responses of students to the 4C’s activity; ask probing questions to help students clarify understanding
Conversations
- Have conversations with students groups about the skills they are using during the cipher activity
Products
- Responses on the 4C’s Recording Sheet
- Ciphers on the Be a Cryptologist reproducible
Evidence of Student Learning
This icon indicates potential assessment opportunities.
Observations
- Observe how students use analytical and problem-solving skills as they encrypt and decrypt simple messages
- Observe the responses of students to the 4C’s activity; ask probing questions to help students clarify understanding
Conversations
- Have conversations with students groups about the skills they are using during the cipher activity
Products
- Responses on the 4C’s Recording Sheet
- Ciphers on the Be a Cryptologist reproducible
Students will:
- Understand what is meant by encryption
- Understand how encryption can be used to keep data safe
- Understand different ways that data can be encrypted
Learning Goals
Students will:
- Understand what is meant by encryption
- Understand how encryption can be used to keep data safe
- Understand different ways that data can be encrypted
Students can:
- Explain why it is important to encrypt data
- Relate the practice of encryption to their own lives
- Use analytical and problem-solving skills to encrypt and decrypt simple messages
Success Criteria
Students can:
- Explain why it is important to encrypt data
- Relate the practice of encryption to their own lives
- Use analytical and problem-solving skills to encrypt and decrypt simple messages
This icon indicates potential assessment opportunities.
Observations
- Observe how students use analytical and problem-solving skills as they encrypt and decrypt simple messages
- Observe the responses of students to the 4C’s activity; ask probing questions to help students clarify understanding
Conversations
- Have conversations with students groups about the skills they are using during the cipher activity
Products
- Responses on the 4C’s Recording Sheet
- Ciphers on the Be a Cryptologist reproducible
Evidence of Student Learning
This icon indicates potential assessment opportunities.
Observations
- Observe how students use analytical and problem-solving skills as they encrypt and decrypt simple messages
- Observe the responses of students to the 4C’s activity; ask probing questions to help students clarify understanding
Conversations
- Have conversations with students groups about the skills they are using during the cipher activity
Products
- Responses on the 4C’s Recording Sheet
- Ciphers on the Be a Cryptologist reproducible
Materials and Preparation
| Material/Technology/Setting | Quantity |
|---|---|
|
1 per student |
Materials
| Material/Technology/Setting | Quantity |
|---|---|
|
1 per student |
- Before beginning the lesson, familiarize yourself with information in the backgrounder and with the activities students will do.
Preparation
- Before beginning the lesson, familiarize yourself with information in the backgrounder and with the activities students will do.
None. This is an introductory lesson.
Student Prior Knowledge and Skills
None. This is an introductory lesson.
| Material/Technology/Setting | Quantity |
|---|---|
|
1 per student |
Materials
| Material/Technology/Setting | Quantity |
|---|---|
|
1 per student |
- Before beginning the lesson, familiarize yourself with information in the backgrounder and with the activities students will do.
Preparation
- Before beginning the lesson, familiarize yourself with information in the backgrounder and with the activities students will do.
None. This is an introductory lesson.
Student Prior Knowledge and Skills
None. This is an introductory lesson.
Teaching and Learning Activities
This icon indicates potential assessment opportunities.
Minds-On: Understanding Data Encryption [10 min.]
| Instructions | Teaching Tips |
|---|---|
|
To begin, have students use the 4C’s Recording Sheet reproducible [Google doc] [Word doc] [PDF], or a similar recording organizer, to document what they learn as they read the backgrounder Keeping Data Safe: Introduction to Encryption. This will allow them to gain knowledge about data encryption and reflect on what they already know. 
Afterwards, have interested students share their responses with the class. |
DiscussionsDiscussion prompts can include:
|
Did You Know?
Encryption plays a very important role in protecting personal information and online data. Encryption hides specific information from everyone except the intended recipient(s). When people interact on platforms like online banking or send an email data encryption protects the sensitive information from cyber criminals (Source: Get Cyber Safe).
Action: Cipher Activity [30 min.]
| Instructions | Teaching Tips |
|---|---|
|
Students will use Be a Cryptologist reproducible [Google Doc] [Word Doc] [PDF] to participate in an encoding and decoding cipher activity. 
Review the instructions on the page with students. Students will work in pairs or small groups to complete the activity. |
LanguageAs students go through the activity, ensure that they understand that:
|
|
Have conversations with students groups about the skills they are using during the cipher activity. |
DiscussionsDiscussion prompts can include:
|
Consolidation: Knowledge Debrief [10 min.]
| Instructions | Teaching Tips |
|---|---|
|
Debrief with the students what they learned during the activity using questions such as the ones on the right. They may need to refer again to the backgrounder. If you wish, the questions could be provided as an Exit Slip. |
DiscussionsDiscussion prompts can include:
|
Background Information for Teachers
Importance of Cryptography
Learning about data encryption is an important step in understanding how to protect private information or sensitive data. Encryption protects data that is sent, received, and stored, regardless of the device, which makes it more difficult for cybercriminals to access.

Image - Text Version
Shown is a colour illustration of a person standing behind a laptop computer in a darkened room, pointing to the screen.
The illustration is in shades of teal and dark blue. It is dark, and the only light comes from the computer screen. The person is wearing a dark hoodie that hides most of their face. They are pointing to a window on the screen that shows a personal profile with a username and password. Next to this is the back of a credit card. Behind the person are lists of information and an email icon.